Cybersecurity has moved from a niche technical role to a core business function. Organizations now treat digital security as essential infrastructure, not optional protection. As cyber threats grow more frequent and sophisticated, demand for skilled professionals continues to rise across industries. This has led many people to ask a practical question: What are the real job requirements for a career in cybersecurity?
- Let’s Deep Dive into the Modern Cyber Security Job Market.
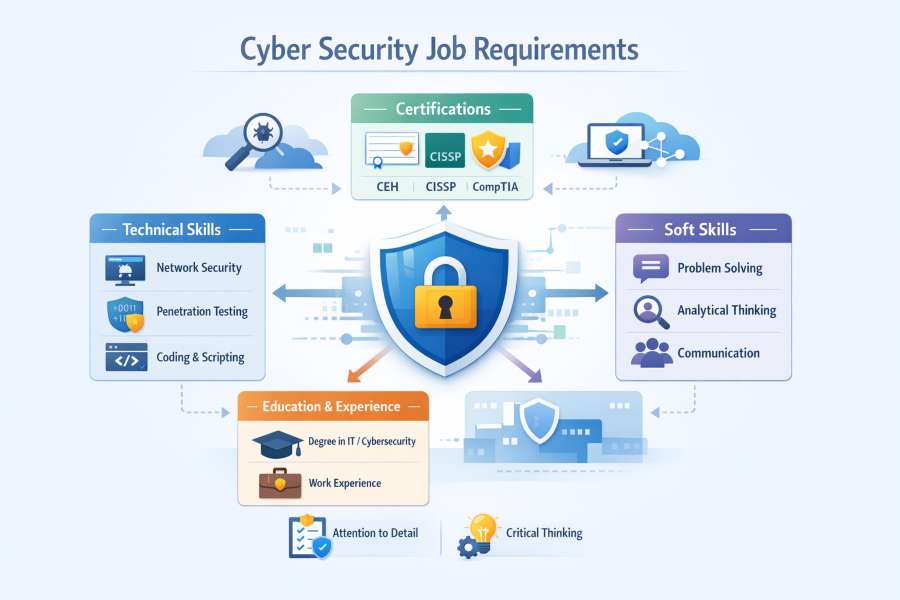
- Core Categories of Cyber Security Job Requirements
- Technical knowledge and skills
- Analytical and problem-solving ability
- Communication and collaboration skills
- Education, certifications, and experience
- Technical Skills Required for Cyber Security Jobs
- Networking fundamentals
- Operating systems knowledge
- Security tools and technologies
- Cloud and virtualization security
- Scripting and automation
- Analytical Thinking and Problem-Solving Expectations
- Communication Skills in Cyber Security Roles
- Educational Background Employers Look For
- Certifications and Their Role in Hiring Decisions
- Experience Requirements by Career Level
- Specialization-Specific Job Requirements
- Security analyst roles
- Penetration testing and offensive security
- Governance, risk, and compliance roles
- Cloud security roles
- Soft Skills That Influence Hiring Decisions
- The Single Most Important Cyber Security Job Requirements Employers Emphasize
- How Employers Evaluate Candidates Beyond Resumes
- How Job Requirements Are Changing Over Time
- Preparing for a Cyber Security Career
- Final Thoughts on Cyber Security Job Requirements
This guide breaks down cybersecurity job requirements in depth. It explains what employers actually expect, how requirements differ by role and experience level, and which skills matter most in today’s market.
Let’s Deep Dive into the Modern Cyber Security Job Market.
Cybersecurity jobs no longer follow a single template. Requirements vary widely depending on industry, organization size, and risk exposure.
Financial institutions, healthcare systems, government agencies, startups, and global tech firms all hire cybersecurity professionals, but they prioritize different capabilities. Some roles focus on hands-on technical defense, while others emphasize risk management, compliance, or incident coordination.
Despite this diversity, most cybersecurity roles share a common foundation. Employers look for professionals who can protect systems, respond to threats, and communicate risk clearly.
Core Categories of Cyber Security Job Requirements
Cybersecurity job requirements typically fall into several broad categories. Understanding these categories helps candidates assess where they fit and what gaps they may need to fill.
Technical knowledge and skills
Nearly every cybersecurity role requires a solid technical foundation. Even non-technical positions benefit from understanding how systems, networks, and applications work.
Analytical and problem-solving ability
Cybersecurity is not about following scripts. Threats evolve constantly, and professionals must analyze unfamiliar situations under pressure.
Communication and collaboration skills
Security teams rarely work in isolation. They coordinate with IT, legal, compliance, leadership, and external partners.
Education, certifications, and experience
Formal education and credentials help employers assess baseline competence, especially for early-career candidates.
Technical Skills Required for Cyber Security Jobs
Technical skills form the backbone of most cybersecurity roles. However, depth and focus vary by specialization.
Networking fundamentals
Understanding how data moves across networks is essential. Employers expect familiarity with protocols, traffic flow, and standard network devices.
Professionals should understand concepts such as routing, switching, firewalls, DNS, and TCP/IP. Without this knowledge, identifying threats or misconfigurations becomes difficult.
Operating systems knowledge
Cyber attacks often target operating system vulnerabilities. Employers value candidates who understand how operating systems function internally.
This includes familiarity with:
-
Windows environments are commonly used in enterprises
-
Linux systems are widely deployed on servers and cloud platforms
Knowing how permissions, processes, services, and logs work is critical for detection and response.
Security tools and technologies
Most cybersecurity jobs involve using specialized tools. Employers do not expect mastery of every platform, but they do expect practical exposure.
Common tools include:
-
Endpoint protection systems
-
Intrusion detection and prevention systems
-
Vulnerability scanners
-
Security information and event management platforms
Hands-on experience matters more than theoretical knowledge.
Cloud and virtualization security
As organizations move infrastructure to the cloud, security responsibilities follow.
Employers increasingly expect familiarity with cloud platforms and their security models. Understanding identity management, shared responsibility models, and cloud-native security tools is becoming a baseline requirement.
Scripting and automation
While not required for every role, scripting skills are increasingly valuable.
Automating repetitive tasks, analyzing logs, and building simple tools improve efficiency and effectiveness. Python is ubiquitous, but shell scripting and PowerShell are also widely used.
Analytical Thinking and Problem-Solving Expectations
Cybersecurity professionals spend much of their time investigating uncertainty. Employers value people who can reason through incomplete information.
Threat analysis and risk assessment
Understanding threats involves more than recognizing malware signatures. Professionals must assess intent, impact, and likelihood.
This requires the ability to:
-
Identify patterns in abnormal behavior
-
Distinguish false positives from real threats
-
Prioritize risks based on business impact
Strong analytical thinking separates effective security professionals from those who rely solely on tools.
Incident response decision-making
During security incidents, time pressure is high. Employers expect professionals to make informed decisions quickly.
This includes deciding when to escalate, isolate systems, preserve evidence, or notify stakeholders. Clear reasoning under stress is essential.
Communication Skills in Cyber Security Roles
Technical expertise alone is not enough. Cybersecurity professionals must explain risks and actions to non-technical audiences.
Reporting and documentation
Clear documentation supports audits, compliance, and continuous improvement. Employers expect accurate reporting of incidents, vulnerabilities, and remediation efforts.
Poor documentation can undermine even technically sound work.
Cross-team collaboration
Security teams interact with IT operations, developers, legal teams, and leadership. Effective collaboration requires translating technical issues into business terms.
Professionals who communicate clearly are more likely to influence decisions and gain trust.
Educational Background Employers Look For
There is no single educational path into cybersecurity, but some common patterns emerge.
Degree expectations
Many employers prefer candidates with degrees in computer science, information technology, or related fields. These degrees demonstrate exposure to core technical concepts.
However, degrees are not always mandatory, especially for roles that emphasize skills.
Alternative education paths
Bootcamps, online programs, and self-directed learning have become more accepted, particularly when paired with demonstrable skills.
Employers increasingly value what candidates can do over where they studied.
Certifications and Their Role in Hiring Decisions
Certifications help employers assess baseline knowledge, especially during initial screening.
Entry-level certifications
These validate foundational understanding and are standard requirements for junior roles.
Mid-level and advanced certifications
More advanced certifications signal specialization and experience. They are often preferred for senior or leadership positions.
Certifications alone do not guarantee employment, but they can open doors and support career progression.
Experience Requirements by Career Level
Experience expectations vary significantly based on role seniority.
Entry-level cybersecurity jobs
Entry-level roles often focus on monitoring, analysis, and support tasks. Employers typically look for foundational knowledge and a willingness to learn.
Hands-on labs, internships, and personal projects can substitute for formal experience.
Mid-level positions
Mid-level professionals are expected to operate independently. They handle investigations, implement controls, and contribute to strategy.
Employers look for proven experience with real systems and incidents.
Senior and leadership roles
Senior professionals are responsible for architecture, strategy, and mentorship. They must balance technical depth with business understanding.
Leadership roles require experience managing teams, budgets, and risk at scale.
Specialization-Specific Job Requirements
Cybersecurity is not a single job. Requirements vary by specialization.
Security analyst roles
Analysts focus on monitoring, detection, and investigation. Employers expect strong analytical skills and familiarity with security tools.
Penetration testing and offensive security
Offensive roles require deep technical expertise and creativity. Employers expect knowledge of vulnerabilities, exploitation techniques, and reporting standards.
Governance, risk, and compliance roles
These roles emphasize policy, regulation, and risk management. Technical knowledge is essential, but communication and documentation skills are equally critical.
Cloud security roles
Cloud security specialists must understand cloud architecture, identity management, and platform-specific controls.
Soft Skills That Influence Hiring Decisions
Soft skills often determine long-term success.
Adaptability
Threats evolve constantly. Employers value professionals who learn continuously and adapt to new tools and attack methods.
Ethical judgment
Cybersecurity professionals handle sensitive data and powerful tools. Trustworthiness and ethical decision-making are non-negotiable.
Attention to detail
Small misconfigurations can have significant consequences. Employers value precision and thoroughness.
The Single Most Important Cyber Security Job Requirements Employers Emphasize
This is the only section that uses bullet points.
-
Solid understanding of networking and operating systems
-
Ability to analyze and respond to security incidents
-
Practical experience with security tools and environments
-
Clear communication with technical and non-technical teams
-
Commitment to continuous learning and ethical responsibility
These core requirements appear consistently across job postings, regardless of specialization.
How Employers Evaluate Candidates Beyond Resumes
Hiring decisions are rarely based solely on resumes.
Technical interviews and assessments
Employers often use scenario-based questions or hands-on exercises to evaluate real-world problem-solving.
Behavioral interviews
Interviewers assess how candidates respond to pressure, uncertainty, and ethical dilemmas.
Portfolio and project review
Personal labs, open-source contributions, and documented projects can significantly strengthen applications.
How Job Requirements Are Changing Over Time
Cybersecurity requirements continue to evolve.
Automation and artificial intelligence are reducing manual work and increasing the demand for strategic thinking. Cloud adoption is reshaping technical expectations. Regulatory pressure is expanding compliance roles.
Professionals who stay current remain competitive. Those who rely on outdated skills risk falling behind.
Preparing for a Cyber Security Career
Meeting cyber security job requirements is a process, not a checklist.
Successful candidates typically:
-
Build strong technical foundations
-
Practice through labs and real environments
-
Develop communication skills alongside technical ones
-
Stay informed about emerging threats and tools
Consistency matters more than speed.
Final Thoughts on Cyber Security Job Requirements
Cybersecurity careers demand more than technical knowledge. Employers look for professionals who understand systems, analyze risk, communicate clearly, and adapt continuously.
Job requirements vary by role and experience level, but the underlying expectations remain consistent. Those who build strong fundamentals and real-world skills position themselves for long-term success in a field that continues to grow in importance.